Table of Contents
Microsoft (Graph) API’s or API permissions for Managed Identities
But you can only add Azure RBAC roles to a Managed Identity, right?
That’s not true, in the blog post below I explain how you can add resource permissions to a Managed Identity.
In my work I mainly use this for Azure Automation. By using Managed Identities I no longer have to worry about secrets or certificates.
I will explain below how we can add permissions to the Microsoft Graph API, but you can also use the steps below for other resources.
What do we need before we can start?
Let’s update managed Identities for the Graph API, but before we can get started we need the following:
- Background explanation
- An account with global administrator permissions
- The AzureAD PowerShell module
- A custom function
Add-ResourcePermissionsToManagedIdentitythat can be found on my personal Github
Background explanation
If you are just looking for the solution, you can skip this step.
A managed Identity is basically an Enterprise application in Azure AD. If it is a system assigned managed identity, it will also disappear when the Azure resource is deleted in Azure.
You can also see the managed Identities under the Enterprise applications in the Azure AD portal. See the screenshot for this.

A Resource is in fact also an Enterprise application. You can often recognize it by the 0000000X AppIds.
Get-AzureADServicePrincipal -all $true | Sort-Object AppId
AppId DisplayName
----- -----------
00000001-0000-0000-c000-000000000000 Azure ESTS Service
00000002-0000-0000-c000-000000000000 Windows Azure Active Directory
00000002-0000-0ff1-ce00-000000000000 Office 365 Exchange Online
00000003-0000-0000-c000-000000000000 Microsoft GraphYou can also see these in the Azure AD portal under Microsoft Applications.
The names are not always recognizable, but the AppId is the same.
Look at the screenshot below for the Microsoft Graph API.

The permissions you grant also receive direct Admin consent, which is why we also log in with a global administrator account.
Please check this post from Microsoft if you want to know more about Managed Identities in Azure:
Managed identities for Azure resources | Microsoft Docs
An account with global administrator permissions
As you probably know you have to give ‘admin consent’ within the portal before a permission becomes active for an app registration. The same goes for a managed identity, but this is done ‘directly’ and cannot be done in the Azure portal.
Neither can you do it with the application administrator role.
That’s why we need the global administrator role.
The AzureAD PowerShell module
Adding the permissions to Microsoft APIs in Azure Active Directory is currently only possible through PowerShell.
For that reason we need the AzureAD PowerShell module.
You can install the module through PowerShell by using cmdlet:
Install-Module AzureAD -Scope CurrentUserOr download it directly from the PowerShell Gallery.
You can log in with Connect-AzureAD with the global administrator account.
A custom function Add-ResourcePermissionsToManagedIdentity
Because it has to be done via PowerShell, I have processed the steps in a PowerShell function.
Copy the function from Github and paste it into your IDE.
Since the function is extensive, we will continue in the steps below.
Let’s add resource (Graph) permissions to a Managed Identity
The function has 3 parameters:
- AppServicePrincipalObjectId
- Permissions
- Resource
ServicePrincipalObjectId
The ServicePrincipalObjectId is the ObjectId as you see it where you enabled the Managed Identity.
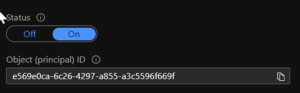
So mine is e569e0ca-6c26-4297-a855-a3c5596f669f.
Permissions
Since I also just released a new PowerShell module for Azure AD & Microsoft 365 reports, I’ll take these permissions from the Microsoft Graph API as an example to add to a Virtual Machine managed identity.
- AuditLog.Read.All
- Directory.ReadWrite.All
- Directory.Read.All
- Reports.Read.All
The permissions generally can be found on Microsoft Docs for the concerning API.
Resource
The Resource is the API name.
The function contains the names with a ValidateSet, so check carefully which name belongs to the API.
The default option is currently the Microsoft Graph API.
If you want to know which resources have which permissions you can use the -ShowPermissionOnly switch.
This can show the permissions for all resources or a specific one.
Add-ResourcePermissionsToManagedIdentity -Resource 'Microsoft Graph' -ShowPermissionsOnly
AllowedMemberTypes : {Application}
Description : Allows the application to read the tenant-level settings of SharePoint and OneDrive, without a signed-in user.
DisplayName : Read SharePoint and OneDrive tenant settings
Id : 83d4163d-a2d8-4d3b-9695-4ae3ca98f888
IsEnabled : True
Value : SharePointTenantSettings.Read.AllWhen you do not enter the resource parameter, you will get a list of all resources with permissions.
Add-ResourcePermissionsToManagedIdentity -ShowPermissionsOnly
AppDisplayName : Microsoft Intune API
AppId : c161e42e-d4df-4a3d-9b42-e7a3c31f59d4
PermissionDisplayName : Manage partner compliance policies with Microsoft Intune.
PermissionDescription : Allows the app to send partner compliance policies and its Azure AD Group assignment to Microsoft Intune without a signed-in user.
PermissionValue : manage_partner_compliance_policy
PermissionType : Application
PermissionId : 3857e233-c379-404e-85e9-bdbf3a62b28f
PermissionIsEnabled : TrueWe stick to Microsoft Graph.
The cmdlet and results
We have the following:
- AppServicePrincipalObjectId: e569e0ca-6c26-4297-a855-a3c5596f669f
- Permissions: Directory.Read.All, AuditLog.Read.All, Directory.ReadWrite.All, Reports.Read.All
- Resource: Microsoft Graph
Now that we have everything together we can use the function.
The function uses the Azure AD module. First sign in with Connect-AzureAD.
I use splatting to make it a bit more visible on my blog.
You can also add the parameters in the normal way.
Add-ResourcePermissionsToManagedIdentity -AppServicePrincipalObjectId 'GUID' -Permissions 'PERM' -Resource 'Power BI Service'The full cmdlet plus results are below.
$ResourcePermissionsToManagedIdentity = @{
AppServicePrincipalObjectId = 'e569e0ca-6c26-4297-a855-a3c5596f669f'
Permissions = @('Directory.Read.All','AuditLog.Read.All','Directory.ReadWrite.All','Reports.Read.All')
Resource = 'Microsoft Graph'
}
Add-ResourcePermissionsToManagedIdentity @ResourcePermissionsToManagedIdentity
ObjectId ResourceDisplayName
-------- -------------------
ychJil06pEGcHIYBHRFH4mzs8YyE6YxFlSPwdQxUGcs Microsoft Graph
ychJil06pEGcHIYBHRFH4lkgUimeWFxNjc7pTvPDWRc Microsoft Graph
ychJil06pEGcHIYBHRFH4s997ZgvvmlOohJ3O5Am45Y Microsoft Graph
ychJil06pEGcHIYBHRFH4kKur_yH5kdAj5gJBGRlVvg Microsoft Graph When adding it for a virtual machine you have to restart the VM for the permissions to take effect.
Optimized.Mga now supports (Graph) Managed Identities!
As you probably saw in the steps above, the Optimized.Mga module now includes an option for Managed Identities. And yes, your AccessToken is still being renewed!
I’ve tested it myself on a Virtual Machine, Azure Automation, and Azure Functions.
Do you come across a Managed identity that it doesn’t work on yet?
Then I’d love to hear about it via Github or the comments below.
You can request an AccessToken as a Managed Identity via the following cmdlet:
Connect-Mga -ManagedIdentityIn addition, a new cmdlet has been added: Show-MgaAccessToken.
With this cmdlet you can immediately see which roles your app registration has.
Connect-Mga -ManagedIdentity
Show-MgaAccessToken -Roles
You've successfully created an AccessToken for the Microsoft.Graph.API
Directory.ReadWrite.All
Directory.Read.All
Reports.Read.AllOptimized.Aza now also supports Managed Identities!
As you probably saw in the steps above, the Optimized.Mga module now includes an option for Managed Identities. And yes, your AccessToken is still being renewed!
I’ve tested it myself on a Virtual Machine, Azure Automation, and Azure Functions.
Do you come across a Managed identity that it doesn’t work on yet?
Then I’d love to hear about it via Github or the comments below.
You can request an AccessToken as a Managed Identity via the following cmdlet:
Connect-Aza -ManagedIdentityIn addition, a new cmdlet has been added: Show-MgaAccessToken.
With this cmdlet you can immediately see which roles your app registration has.
Connect-Aza -ManagedIdentity -Resource 'https://management.azure.com'
You've successfully logged in to https://management.azure.com
Hello Bas
I have followed up your tutorial
I have created a user assigned Managed Identities in Azure
I have added all the permissions I wanted to Microsoft graph
If I am trying to use MGA with Connect-Mga -ManagedIdentity
I have an error Cannot find Managed Identity Type…
And I am not sure of the permissions assigned to the Managed Identity…as it seems to return all permissions granted to Graph…and not the combination of Graph and Managed Identity